Did you know that email is the #1 means used by hackers to access your data or to launch phishing, trojan, malware or ransomware attacks? And, unfortunately, these email cyber attacks are increasing in frequency and no one is immune.
Here are some facts and figures around email cyber attacks, ransomware, phishing, and other online threats:
- 97% of IT service providers agree that ransomware attacks on small businesses are becoming more frequent, a trend that will continue over the next 2 years.
- Leading causes of ransomware infections are phishing email scams followed by a lack of employee awareness.
- The most common impact of a ransomware infection is business-threatening downtime, followed by lost data and/or devices.
- Average ransoms requested are typically between $500 and $2,000, however 10% of ransoms are over $5,000.
- 1 in 4 people who have paid the ransom don’t get their data back.
Businesses of all sizes are at risk of email cyber attacks, so it’s vitally important that all your employees are aware of the ‘red flags’ that indicate an email is suspicious.
Here are the 7 red flags that your staff need to be aware of when they’re opening emails:
1. Check out the “from” address
Have a close look at the “from” email address: hackers often make themselves look like a person or company you know, but in actual fact it’s a spoof.
A common way they do this is to misspell the address, for example:
Real email: service@intl.paypal.com
Hacker’s email: service@intl.paypall.com
… Notice the additional “l” in “paypall” in the spoofed email. At first glance the email appears to be legitimate, but the domain isn’t accurate.
Or sometimes hackers put additional characters into the email address, for example:
Real email: appleid@id.apple.com
Hacker’s email: applied@identity.apple.com
… Notice that the hackers use “identity” rather than “id” in the domain.
These differences can be extremely subtle, so look closely and carefully.
2. Look at the “to” line
Hackers sometimes send one email to many people by using the CC or BCC option. So if you see lots of people you don’t know in the CC line, that should raise a red flag.
Ditto if the email address in the “to” line isn’t yours – that’s a sign you’ve been BCCd (blind carbon copied).
3. Evaluate the subject line
Hackers often try to trick people with scare tactics, or something that requires immediate action.
So subject lines such as “Change password immediately”, “Your account has been compromised”, “Need wire transfer now”, or “Claim your prize now” should immediately raise red flags.
Of course, there’s a chance that an email such as this could be legitimate, so be sure to validate the source before you take any action.
And if the email is from a bank, service or organisation that you don’t have an account with – that should raise an additional red flag.
4. Review the content
If you received an email that urges immediate action, and you’re still not sure if it’s legitimate or not, slow down and evaluate the content carefully. Do not click any links or open any attachments!
The sender of the email ask you to urgently update your information, or change your password. Treat any emails with this kind of content with great suspicion.
Also, take a look at the spelling and grammar in the email: if there are spelling mistakes, there’s a good chance it’s an email cyber attack. Big, respected companies do not generally send emails with typos and spelling mistakes!
5. Check the hyperlinks – without clicking them
Also as part of checking the content, pay attention to any hyperlinks within the email.
You do this by hovering over the link with your mouse, and see if the link looks genuine. You do that by looking at the status bar at the bottom of your browser, to see if the website address being linked to is as it appears. If the URL does not match what the text says, do NOT click on the link, and delete the email.
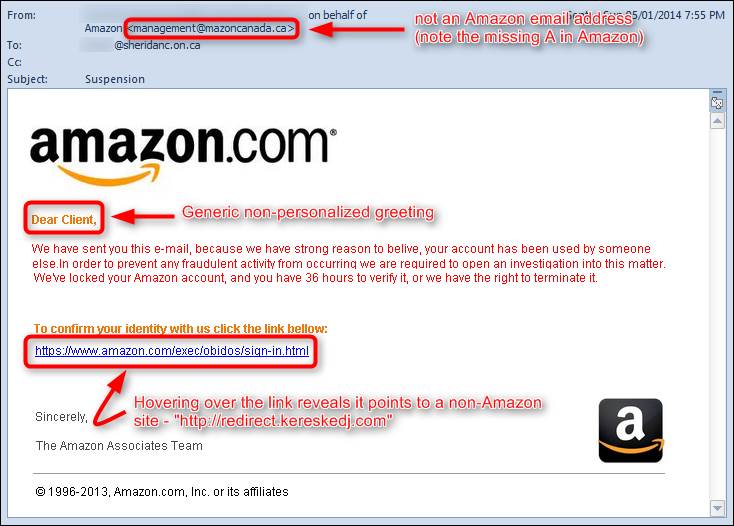
Here’s an example of a phishing email that demonstrates both a fake hyperlink, and a false From address:
6. Consider the time of day the email was sent
If you get an email and you’re not sure if it’s suspicious or not, also check the time of day it was sent, and the time zone the sender is in. For example, it’s highly unlikely that a New Zealand business will be emailing you at 2am!
7. Look carefully at any attachments – without opening them
Email cyber attacks often contain attachments that contain a malicious virus or other type of malware. So never open any attachments that you’re not expecting, and especially attachments with .exe at the end.
Still not sure if the email is genuine or not?
If you are in any doubt at all whether an email is genuine or a cyber attack, check with your IT administrator or forward the email to Optimus Systems (support@optimus.co.nz) and we will check it out for you.
Prevention is better than cure when it comes to email cyber attacks
Making your team aware of these 7 red flags is vital in staying safe. But, as the saying goes, prevention is better than cure, so also ensure you have layered protection in place:
- Web filtering: Stops web-based viruses or malware attacks before they enter your network. Find out more about web filtering.
- Mail filtering: Quality spam protection and mail filtering is a must for businesses of all sizes, whether you’re using an email server or a cloud-based service. Find out more about mail filtering.
- Business continuity backup services: Why risk losing your data, when automated online backups are simple to set up, and also affordable? Find out more about business continuity and backup services.
With these online security services in place – as well as a workforce that knows how to distinguish genuine emails from cyber attacks – you have far less chance of your IT system being the victim of a virus, malware, trojan, or ransomware.